- Minimalist Gmail is the Best Gmail Tweaker for Chrome Yet (Chrome)
Adding extra features to Gmail isn't a new idea, but Minimalist Gmail for Chrome is the best tweaker yet: You can hide items, add row highlights, and even change the five Google links at the top of the page. - LibreOffice 3.3 Final Gives the OpenOffice.org Suite a Fresh Start (Windows/Mac/Linux)
The first finalized release of the OpenOffice.org spin-off, LibreOffice, has hit the web at version 3.3. It's got a few unique features, an ever-so-slightly tweaked look, and the ability to export to Microsoft's DOCX format by default. - WidgetLocker Customizes The Sliders on Android's Lock Screen (Android)
The unlock and sound sliders on Android are handy, but if you'd like quick access to other things from the lock screen, WidgetLocker willl let you add anything from widgets to app shortcuts to extra sliders. - Home Dash Makes Firefox a (Useful) Full Screen Browser (Firefox)
Most browsers offer a "Fullscreen Mode," but still rely on the same address bar, tabs, and other mechanisms to get you around. Home Dash reconfigures Firefox for quick searching and browsing without any toolbar whatsoever. - Week Cal Is a Powerful, iCal-Like Replacement for iOS' Default Calendar App (iOS)
The iPhone's Calendar app is handy, but it frankly leaves a bit to be desired. If you'd like a more powerful, iCal-like interface for your iPhone, Week Cal is a great calendar replacement app. - Splice Is a Free, Feature-Rich Video Editor for iOS (iOS)
Instead of paying for Apple's iOS version of iMovie, Splice is an alternative video editor that you can use for free. It comes with many of the same features you'll find in iMovie, but without the cost. - Briss Trims PDFs so They Fit Better, Are Easier to Read on Your Ereader (Windows/Mac/Linux)
Virtually every current ereader offers native support for the PDF format, but no PDF was designed for your ereader's 5-7" screen. Briss, a cross-platform open-source tool, gives you several ways to trim PDFs to look better on your ereader. - Seek Droid Is the Simplest Way to Find Your Lost Android Phone (Android)
We've featured a few different methods and apps for finding your lost phone. With the $0.99 Seek Droid, however, you can locate your device, remotely lock it, wipe it, and even see your recent calls with almost no effort. - BootXChanger Customizes Your Mac OS X Boot Screen (Mac)
Tired of the old gray apple that greats you every time you load up Mac OS X? BootXChanger provides an easy, drag-and-drop method of changing the default image to just about anything you want. - K-9 Mail Is What Android's IMAP Email App Should Be (Android)
If you don't use Gmail or Google Apps, the default email experience on Android is, honestly, pretty cruddy, unless Motorola or HTC fixed up your Email app. K-9 Mail cleans up, optimizes, and just plain fixes Android's default Mail app.
Monday, January 31, 2011
Top Downloads
Five Best Windows Timer Applications

Earlier this week we asked you to share your favorite Windows timer application. We rounded up the nominations for a vote and now we're back to highlight the five top picks and put them before you for a vote.
Orzeszek Timer (Free)

Orzeszek Timer won many readers over with a dead simple interface that allows you to input your count down needs with flexible formatting. Orzeszek Timer recognized, for example, "5" as five minutes, "1d 3h 8m 30s" as one day, three hours, eight minutes, and thirty seconds, and can even recognize future date and time combinations for those long haul count downs. Orzeszek Timer also accepts command line arguments so you can make batch files for your most frequently used countdown values. No Installation required.
Focus Booster (Free)

Focus Booster is a free Adobe-Air based timer implementation (it's also available for Mac OS X) that sports a sleek interface and built in break timing. From the options menu you can adjust your session length, your break length, toggle a ticking background sound on and off (great if you like the motivation ominous ticking provides), and toggle the main alarm sounds on and off. Focus Booster has a slick meter-style count down so not only do you see the time counting down but, for the more visually oriented among us, you see the bar slowly fill as the seconds are marked off. When the bar is completely green your time is up.
CookTimer (Free)

CookTimer is a simple countdown timer with presets for 3/5/10/15 minute blocks of time as well as a custom user input. CookTimer will, if toggled to do so, automatically reset and begin the count down again and continue to ring until attended to (handy if you're the kind of person that can hear a chime and become distracted before you deal with what the chime represents). CookTimer is also available for Linux.
SnapTimer (Free)

SnapTime appears, at first glance, like many of the other tiny one-function timers available. Delving into the options menu reveals a slew of settings, however, that allow you to customize the alarm sound, display a message, push a system tray notification, run a program, change the display font, loop the alarm, set it to automatically restart, and more. No installation required.
CoolTimer (Free)

CoolTimer, most notable perhaps for the shockingly pink default color scheme, is a classic in the timer app world. Some readers have been using CoolTimer for as long as they can remember using timer apps on their computers. It sports an easily adjusted counter as well as support for multiple preset times. You can use the built in sounds or load your own audio files and it functions as an alarm clock, a count down timer, and a stock watch. Timers can also have accompanying notices in order to remind you why you set the time.
LastPass Browsers Autofill Logins on iPhone and iPad


LastPass has always been available on iOS via a couple of bookmarklets, but that sure isn't the same than the constant-autofill experience you get on the desktop. Since mobile Safari doesn't allow for any sort of plug-ins, LastPass opted to create an entirely new browser, so you could speed through the login process without any sort of workarounds. The iPhone app requires the (remarkably cheap) $12/year premium subscription, but the iPad app is free for all users.
Apart from LastPass integration, these browsers don't have a ton of other features. The iPad browser does have tabs (which is awesome), and while it doesn't quite measure up to previously mentioned Perfect Browser, having that integration is awesome when I'm jumping between apps like Facebook, Gmail, and other webapps. There are definitely a few bugs in the password manager portion of the app, but if you can get past that—which I personally can, since I really just want it to input all my passwords for me—it's a pretty handy app to have around, especially if you're not looking for a super-advanced browser.
LastPass and LastPass Tab are free downloads for iPhone and iPad, respectively. The iPhone app requires LastPass' premium subscription, while the iPad app is completely free
3 Tutorials to Check Out This Weekend: Crisis Edition

The situation in Egypt has colored much of our coverage today, so it's only fitting that we send you into the weekend with some relevant tutorials: an introduction to Ushahidi for developers, tips for optimizing CouchDB and how to create a Tor relay.
Ushahidi 101
Ushahidi is a non-profit organization that develops open source technology for disaster response. We've covered how its been used to visualize floods in Queensland, for example.Above is a brief introduction to its technology for developers.
Disclosure: ReadWriteWeb contributor Pete Warden recently joined parent organization SwiftRiver as we reported here.
CouchDB Optmization
CouchDB is great for building Web applications that need to function when Internet connectivity is sporadic. CouchDB sponsor company CouchOne has a case study on how aid workers in Africa are using it to manage health data.Mu Labs recently published a tutorial called "Notes and tips on optimizing CouchDB performance" for developers who want to squeeze as much performance as possible out of CouchDB.
Tor
As we reported earlier there's been a spike of Tor usage in Egypt the during the past couple days as the government there has severely restricted Internet access. Many on Twitter are calling for users to host more Tor relays. Here's how to configure one.4 Reasons to Spring A Few Bucks For That Premium Wordpress Theme
 When it comes to launching blogs and Websites, small businesses often go with Wordpress, and for great reasons: it's customizable, widely-used and - best of all - free. In addition to the core product, there are tons of free plugins and themes available that make building out the ultimate site a cinch.
When it comes to launching blogs and Websites, small businesses often go with Wordpress, and for great reasons: it's customizable, widely-used and - best of all - free. In addition to the core product, there are tons of free plugins and themes available that make building out the ultimate site a cinch. Sure, we all love free stuff. But just because there are hundreds of free options within reach doesn't mean you shouldn't be willing to spend a few dollars.
Enhanced Security
To be fair, most free Wordpress themes do not contain vulnerabilities of this sort. As Ambrose recommends, you can safely download legitimate, free themes from Wordpress.org, Smashing Magazine and Woo Themes, among others. But in general, premium themes are probably less likely to come with security issues than free ones. If problems do arise, many premium themes come with technical support to help troubleshoot them.
Better Design
Let's face it: In many cases, when a site is sporting a free Wordpress theme, you can tell. A surprising number of business sites even go with the default theme or another very popular option. For personal blogs, this can be forgiven. For businesses, it can look unprofessional.
Even though there are quite a few free themes that look premium, on the whole, the ones that cost a few bucks are more professionally-designed. It's worth investing a little bit to help your site stand out in the cookie-cutter crowd.
We rounded up six especially attractive Wordpress themes for small businesses, but that's only a small sampling of what's available.
We can't overstate the importance of design when it comes to business sites, especially if your site is used to sell products or capture leads. When a crummy-looking site or bad user experience can mean the difference between a completed transaction and a disgruntled would-be customer, investing in a good design is worth it.
While It's Not Free, It's Also Not Expensive
Small businesses are justifiably a budget-concious lot. That's what makes open source products like Wordpress so appealing. Yet while premium Wordpress themes are not free, they're still pretty cheap. Consider it could cost thousands of dollars to get a professional design firm to give your site a facelift, paying $20 or $50 is a drop in the bucket.A membership to the high-quality theme directory Elegant Themes only costs $39 per year. A subscription gives you access to over fifty premium themes, with new ones being released all the time. Other examples include WooThemes, Premium Wordpress and Theme Forest.
Customization and Documentation
Anyone who knows their way around HTML, CSS and basic PHP can customize pretty much any Wordpress theme, but many premium theme developers make it easier by providing detailed documentation and, in many cases, the original Photoshop PSD files for easy graphics manipulation.
Another perk of premium themes is that many of them offer more options for customizing your site's appearance from the Wordpress admin. For example, Elegant Themes come with their own settings area called ePanels, from which you can control graphics, color schemes, SEO settings, advertisting, the site's navigation and some aspects of its layout. Many of these things are typically only editable at the theme level, which obviously requires some coding ability.
Hidden commands in windows …
Without mysteries, life would be very dull indeed. What would be left to strive for if everything were known?
Just like the commands of Windows, The true mystery of the world is the visible, not the invisible. If you turn the pages and insert your head in the basic of Windows then there are some thing to explore, here are few examples of some hidden secret commands in Windows:
Go to the Command Prompt in the Accessories menu from the All Programs start button option, and then type ‘systeminfo’. The computer will produce a lot of useful info, including the uptime. If you want to keep
these, type ‘systeminfo > info.txt‘. This creates a file called info.txt you can look at later with Notepad. (Professional Edition only).
Poking around in gpedit will reveal a great many interface and system options, but take care — some may stop your computer behaving as you wish.
(Professional Edition only).
user32.dll,LockWorkStation‘ in the location field. Give the shortcut a name you like. That’s it — just double click on it and your computer will be locked. And if that’s not easy enough, Windows key + L will do the same.
Find that out by typing ‘tasklist’, which will also tell you a lot about what’s going on in your system.
can make XP leave zip files well alone by typing ‘regsvr32 /u zipfldr.dll‘ at the command line. If you change your mind later, you can put things back as they were by typing ‘regsvr32 zipfldr.dll‘.
Just like the commands of Windows, The true mystery of the world is the visible, not the invisible. If you turn the pages and insert your head in the basic of Windows then there are some thing to explore, here are few examples of some hidden secret commands in Windows:
1. ‘systeminfo’
It boasts how long it can stay up. Whereas previous versions of Windows were coy about how long they went between boots, XP is positively proud of its stamina.Go to the Command Prompt in the Accessories menu from the All Programs start button option, and then type ‘systeminfo’. The computer will produce a lot of useful info, including the uptime. If you want to keep
these, type ‘systeminfo > info.txt‘. This creates a file called info.txt you can look at later with Notepad. (Professional Edition only).
2. gpedit
You can delete files immediately, without having them move to the Recycle Bin first. Go to the start menu, select Run… and type ‘ gpedit.msc‘; then select User Configuration, Administrative Templates, Windows Components, Windows Explorer and find the Do not move deleted files to the Recycle Bin setting. Set it.Poking around in gpedit will reveal a great many interface and system options, but take care — some may stop your computer behaving as you wish.
(Professional Edition only).
3. rundll32.exe
You can lock your XP workstation with two clicks of the mouse. Create a new shortcut on your desktop using a right mouse click, and enter ‘rundll32.exeuser32.dll,LockWorkStation‘ in the location field. Give the shortcut a name you like. That’s it — just double click on it and your computer will be locked. And if that’s not easy enough, Windows key + L will do the same.
4. sysoc.inf
XP hides some system software you might want to remove, such as Windows Messenger, but you can tickle it and make it disgorge everything. Using Notepad or Edit, edit the text file /windows/inf/sysoc.inf, search for the word ‘hide‘ and remove it. You can then go to the Add or Remove Programs in the Control Panel, select Add/Remove Windows Components and there will be your prey, exposed and vulnerable.5. schtasks
For those skilled in the art of DOS batch files, XP has a number of interesting new commands. These include ‘eventcreate‘ and ‘eventtriggers‘ for creating and watching system events, ‘typeperf’ for monitoring performance of various subsystems, and ‘schtasks’ for handling scheduled tasks. As usual, typing the command name followed by /? will give a list of options — they’re all far too baroque to go into here.6. ipv6
XP has IP version 6 support (the next generation of IP). Unfortunately this is more than your ISP has, so you can only experiment with this on your LAN. Type ‘ipv6 install‘ into Run… (it’s OK, it won’t ruin your existing network setup) and then ‘ipv6 /?‘ at the command line to find out more. If you don’t know what IPv6 is, don’t worry and don’t bother.7. taskkill
You can at last get rid of tasks on the computer from the command line by using ‘taskkill /pid‘ and the task number, or just ‘tskill’ and the process number.Find that out by typing ‘tasklist’, which will also tell you a lot about what’s going on in your system.
8. zipfldr.dll
XP will treat Zip files like folders, which is nice if you’ve got a fast machine. On slower machines, youcan make XP leave zip files well alone by typing ‘regsvr32 /u zipfldr.dll‘ at the command line. If you change your mind later, you can put things back as they were by typing ‘regsvr32 zipfldr.dll‘.
20 Common Mistakes To Avoid By Any Internet Surfers
Novice Internet surfers are eager to explore World Wide Web known for researching, shopping, communicating and enjoying the media. And then there are evil waiting to trap these greenhorns and make money out of it. Identity theft, Email Spamming, Chat Room etc are some of the common traps people fall in to.
But that doesn’t mean one should avoid using Internet, as today most of us keep in touch with friends, family, and locate cool places or news by Internet. One only needs to be careful while surfing Internet in order to save time and to remain at the safer side. If you are someone wanting to start your web journey then make a note of these common mistakes to avoid when surfing online.
But that doesn’t mean one should avoid using Internet, as today most of us keep in touch with friends, family, and locate cool places or news by Internet. One only needs to be careful while surfing Internet in order to save time and to remain at the safer side. If you are someone wanting to start your web journey then make a note of these common mistakes to avoid when surfing online.
- Avoid login on third party applications which require email logins.
- Avoid accessing account through any email link as it can be risky. If the email turns out to be fraudulent then cyber criminal will have access to your account information.
- Avoid having single password or PINs for accessing all your online accounts, this can again lead to identity theft.
- Avoid using unsafe site that does not come with term ‘https‘. The “S” stands for secure and you should always make note of it before accessing any site.
- Avoid clicking on pop-ups that says “Your Pc is Insecure”, such links can have malware automatically downloaded to your PC.
- Avoid downloading free stuffs such as screen saver and those stupid smiley faces. Such things are very dangerous to your PC and you will soon notice it has turned slow then earlier. Sites like download.com are safe to use.
- Be careful with those phishing mails, they may create a sense of urgency as “Your Account is in Risk” or an “Unauthorized transaction has taken place” so send your account details. Remember any bank will not ask your account detail via mail.
- Make sure you always have updated antivirus software in place.
- Always check with your bank if they have any additional security for your online transactions, such as IPIN’s or Zero liability card.
- Always have your CC details save in real world. Do not share it with anybody via sending mails or over even on telephone.
- Never forget to delete the system’s cache, passwords or history, it could easily lead to identity theft and stolen bank and email information.
- You have won a lottery and or an IPod are the common terms used by spammers to trap you, avoid falling to such traps.
- Always blacklist the spammers you come across in mails without just deleting the spam mails.
- Don’t ever click on the Close window without logging of your account especially if you are at cybercafé for accessing Internet then you are more at risk.
- Always have a back up for your emails just as how you keep a hard copy of your important docs and other things.
- Avoid believing in those brainless “Microsoft Is Sharing Its Fortune” kind of mail, they are just spammers requiring your details to trouble you more.
- Always have a habit of not clicking on phishing email, the goal of phisher is to fool you for entering your details into something that actually appears to be safe and secure, but in reality is just a fake site set up by the scammer.
- Avoid giving your full name, home address, phone number, Social Security number, passwords, names of family members, credit card numbers online. Best is to remain anonymous and enjoy surfing
- Never forget to scan the attachment you receive in your mail box. Virus attacks are mostly through such attachments.
- Social networking sites are something we cannot avoid these days, yet it is always secure to follow known person on Twitter or to add on Facebook. Don’t forget to do security check if you tend to add unknown person.
Sunday, January 30, 2011
Turn Your Desktop Into a Real 3D Multi-Touch Desktop Now

The way a Windows desktop behaves, has not been changed since thirteen years. Its all the same, rough and rigid icons lying dumbly at the cold desktop. Now is the time you can give your desktop a little extra. Bring your desktop to real 3 Dimensional life like. Arrange icons in a pile or groups. It takes just a few clicks or your finger movements to do with all the data at your desktop to arrange it in the way you want it in a real 3D environment.
BumpTop is a fun, intuitive 3D desktop that keeps you organized and makes you more productive. Like a real desk, but better. Now with awesome mouse and multi-touch gestures, you will experience your desktop as never before. Your desktop doesn't have to be a boring graveyard for lost and forgotten files anymore! Transform it with BumpTop. Create the desktop that suits your needs and style. MAC and Linux versions are also available.
Desktop 3D Enhancement
Saturday, January 29, 2011
Here's Some Utilities To Delete Hidden Metadata Information....
Doc Scrubber – Metadata Removal Software


At this juncture comes Doc Scrubber which is of course free and can be used to remove hidden as well as data or documents that my turn out to be embarrassing potentially. Just go ahead by selecting all the relevant data in a particular folder and have the Metadata purged all at once, advantage being you saving your precious time as well as efforts this way.It is tested and found to be compatible with Word 97, 2000, and XP documents.

Stripper – Remove Jpeg Metadata
The under demonstrated screen shot depicts as to how you can manually remove the Metadata for each Microsoft Office Doc and Docx files.The list may vary right from having author’s name, last printed, last edited sort of categories and may therefore turn out to be huge.The only problem it encompasses is its inability to batch edit the doc files, that may range to hundreds.


At this juncture comes Doc Scrubber which is of course free and can be used to remove hidden as well as data or documents that my turn out to be embarrassing potentially. Just go ahead by selecting all the relevant data in a particular folder and have the Metadata purged all at once, advantage being you saving your precious time as well as efforts this way.It is tested and found to be compatible with Word 97, 2000, and XP documents.

In addition to the removal of metadata, it can well produce the complete analysis of metadata as to know what it has in it.
Stripper – Remove Jpeg Metadata
Strip / clean / remove unnecessary Metadata (junk) from JPG / JPEG / JFIF & PNG files using a special tool named Jpeg And PNG Stripper.The image quality remains unaffected and can well be used to hide sensitive camera properties as well as settings used.
Friday, January 28, 2011
Hey Facebook.ers.... & twitter..ers It's For You
Now you can set your facebook status and tweet's just by selecting text in your Firefox browser.
It is quite common that we come across several quotes or lines that we like them and also wish to share them either on Twitter or Facebook, but find it boring to cut, copy and paste the stuff. But not now. Statusus is a Mozilla Firefox extension that allows setting a Facebook status or Twitter's tweet by highlighting text from any website.

All you have to do is simply
It is quite common that we come across several quotes or lines that we like them and also wish to share them either on Twitter or Facebook, but find it boring to cut, copy and paste the stuff. But not now. Statusus is a Mozilla Firefox extension that allows setting a Facebook status or Twitter's tweet by highlighting text from any website.

All you have to do is simply
- Highlight and right-click the desired text.
- And set your status via the Statusus option.
Beef Up Your Password by Memorizing a Few Key Codes

We've seen how easily weak passwords can be hacked, and we've also discussed how you can easily memorize or automatically generate and fill in secure passwords. Here's a great technique to add an extra layer of security to your
password.
If you're a Windows geek, you may be familiar with the Alt + numeric pad key combination that creates ASCII and Unicode characters which are not present on a regular keyboard.
These characters are less frequently included in brute force or dictionary attacks, which can act as first line of defense for your password against cracking. Many keyloggers would also not be able to log most of the characters from the ASCII code chart, which would render them useless.
Update: As some readers have pointed out, not all of the codes available to Windows Alt+key code combinations are ASCII—some are non-ASCII codes, which can work, but are sometimes not supported by web sites. They'll still add extra obscurity to your password, but you would not want to use an all non-ASCII password.
If someone tried to guess your password and you have any ASCII character in it, they would need to know the exact key combination for that character before they get anywhere. In a way, the ASCII codes act as a password for your password.
Here is how it works:
When you press Alt + 16 in any text field in Windows, it will create a ► character and pressing Alt + 17 on the num pad gives a ◄. Go ahead, open up notepad and try it out or just open the Run dialog and try out any Alt + number combination.I generally use a single ASCII character at the start and end of the password. So it looks something like ►mypassword◄.
ASCII characters are part of the US-ASCII code, which is the numerical representation of a character such as 'a' or '@' or any key combination we use. Since these characters are recognized by all applications on Windows, they can be used anywhere. Including a couple of characters from the ASCII table in your password allows us to create some really tough passwords to crack
Ubuntu Tips Applet Fills Your Brain with Useful Command Line Knowledge


Ubuntu: Most "tip" widgets are intrusive and geared toward beginners, but the Ubuntu Tips applet is actually pretty neat, giving out surprisingly good command
line tips at a specified interval, so you can expand your Linux knowledge as you work.
Ubuntu Tips uses Ubuntu's built-in notification system to dole out small Linux tips every few minutes (or however long you want). It focuses on the command line, and even if you've been using Linux for awhile, there are probably some tips in there you don't know. I was pretty surprised at the quality of tips, and I ran across quite a few I didn't know. Of course, you can always start with our guide to time-saving Terminal shortcuts, too—but this applet is a pretty good supplement once you start working in the command line a bit more. Hit the link to check it out.
The Ubuntu Tips Applet is a free download for Ubuntu systems.
Become a Command Line Ninja With These Time-Saving Shortcuts

Image remixed from an original by xkcd.
Power users love the command line for its ability to perform complicated tasks with just a few keystrokes. But for beginners who don't know the shortcuts and type everything out longhand, it can seem like it takes forever (I know this because I'm just past beginner myself, and I still didn't know most of these shortcuts).
From simple keyboard shortcuts to built-in shorthand to commands you can build and customize yourself, the Terminal has a ton of ways you can speed up your command line work, and here we're going to show you some of the basics (as well some customizable features that you can use to shorten pretty much any command you want).
If you're just getting started with the command line, we recommend you also check out our command line primer for beginners. Heck, even if you're not a beginner, skim through it—you're sure to find a few things you didn't know. We'll be touching on a few of those subjects and building on them here, too.
Keep the Windows Desktop from Crashing by Sandboxing Explorer Windows
 The Explorer process runs a lot of important things in Windows, and when it crashes, it can really slow you down. It turns out, however, that you can sandbox Explorer windows so if one crashes, it doesn't drag your whole system down.
The Explorer process runs a lot of important things in Windows, and when it crashes, it can really slow you down. It turns out, however, that you can sandbox Explorer windows so if one crashes, it doesn't drag your whole system down.One option in Windows Explorer that I find extremely useful is the option to separate out the taskbar and desktop from the other open Explorer windows in two different
explorer.exe processes. This makes sure that the taskbar and desktop stay alive if explorer.exe happens to crash, which it does quite often in my experience.This is especially useful in computers that are used by not so computer savvy people, who won't know to hit Ctrl+Shift+Esc and run
explorer again in case of a crash. I find it a timesaver too, because I experience lots of crashes when exploring my phone memory in Explorer via Bluetooth.In Windows 7, there is a straightforward option in Windows Explorer under Tools > Folder Options > View > Launch Folder Windows in a Separate Process (Not to be confused with "Open Each Folder in a Different Window" under the General tab).
In Windows XP and before, a registry hack will do the same thing. Open up Regedit and go to
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer, right-click in the right pane and create a new DWORD called DesktopProcess with value 1.Note that sandboxing this process will be a bit more resource intensive than keeping them as one process. However, if you've got fairly recent hardware, this'll probably be a welcome change. Now, if and when Explorer crashes, you'll only lose that window and not your entire desktop.
Wednesday, January 26, 2011
For Better transfer Rate......Have Less Hard Disk Partitions
Speaking of hard disc speed and transfer rates, two hard disks are better than a larger (SATA) one. It is a statistically proven fact that that the seek time is the least in the first partition on your hard disk drive.
When a HARD DISK is partitioned, the first partition i.e the ‘C’ dive has always the best speed as compared to the subsequent drives. There is a fall in transfer rates as we go form C to D to E and so on. Not more than two partitions is a good idea because too many partitions may slow down the average seek time and transfer rates. Throughput in the 2nd partition may have a 50% fall in speed as compared to the 1st.
So try to use two 500 GB Hard Disks instead of a 1TB Hard disk.
Speed Up Your System
Slow Speed a common and a biggest problem with all the people who generally uses desktop or laptops which can be attributed to a number of factors. Most of
us are always worried as our systems run very slowly or have a very slow startup. This is mainly because of two reasons:
- Malware Attack.
- Improper system settings.
So, there are various settings in our system that should be configured in the right manner to help the system run at a faster speed and give better performance. There are many tools which assist on the automatic configuration of these settings.
So,here is the solution of all your problems the WinMate, which is a system optimize tool available for free and can be used to fix the poor settings. WinMate can hence make your system run in the most favorable state.
Additionally, WinMate presents one with a broad variety of great utility and security software. This software is conceived to optimize our experiences with the system and also speeds up the startup.

- The high-performance detection algorithm is employed by WinMate to speedily find Windows errors and hence to avert the computer from freezing, crashing and getting Blue Screen.
- Furthermore, WinMate fixes slow computer and sluggish startup, as discussed before. It hence guarantees a better and safer environment of your Internet Explorer browser as it has many in-built IE tools.
- WinMate also supplies valuable system devices like File Wiper, Drive immuner, Program Uninstall.
- So, overall it completely protects the system.
Now Keep Your Operating System Always With You Part 2
As per my last post (Now Keep Your Operating System Always With You - Make Pocket OS) now you know how to make portable operating system you must want some application to be must run on your system.
Yes that's possible you just need to download them application you needed, give them executing permission and rook you can run them just at a single click
 |
| click on image for a closer look |
Download them hear
http://www.portablelinuxapps.org/
Google Launches Limited Version of "Google Offers" Coupon Service
We recently found out that Google was readying a Groupon clone called Google Offers, and it looks like they've already started releasing the service (albeit in a
limited format). To see offers, you can just do a Google search for
coupons site:maps.google.com intitle:Google Offers to see the 41,500 results already available. If you'd like to see coupons available near you, there is an iGoogle gadget that can search by location. The deals aren't anything spectacular like Groupon or other similar services, but it's a nice gadget to stick in your iGoogle and check out when deciding where to go for lunch that day. Obviously, there will be quite a few more deals once Google officially launches the service, too. Hit the link to read more. [via TechCrunch]Disable Constant Font Cache Rebuilding in VLC
VLC is certainly one of the greatest media players around, but some people have been noticing an annoyance in which it "rebuilds the font cache" nearly every
time you start it up. Here's how to disable that behavior.
Rebuilding the font cache not only takes time, sometimes it can make VLC hang completely, which can get old quickly. To make it stop, just open up VLC and go to Tools > Preferences. Hit the "All" radio button in the bottom left hand corner, then go to Video > Subtitles/OSD in the left-hand pane. In the Text Rendering Module dropdown, pick "Dummy Font Renderer Function" and hit save. The next time you open VLC, you should be free of that annoying cache-building dialog.
Detect Naughty Pictures and Video with Nude.js

No, Nude.js isn't a Node.js parody or alternative. In fact, I was kind of disappointed to discover that it wasn't. I've become that special sort of geek that would rather read about server side JavaScript than about nudity.
But this is actually pretty cool. It may seem prudish, but if you have antiporn rules you need to enforce on any sort of Web app that allows uploads, this could be helpful. The author, Patrick Wied, suggests it could be used in client-side proxies to ensure child-safe surfing.
Working
- You use your web browser to make a request for "/about.html" on a Node.js web server.
- The Node server accepts your request and calls a function to retrieve that file from disk.
- While the Node server is waiting for the file to be retrieved, it services the next web request.
- When the file is retrieved, there is a callback function that is inserted in the Node servers queue.
- The Node server executes that function which in this case would render the "/about.html" page and send it back to your web browser.
Firefox Trick for super speed browsing!
Reduce the amount of RAM Firefox uses for it’s cache feature
Here’s how to do it:
1. Type “about:config” (no quotes) in the adress bar in the browser.
2. Find “browser.sessionhistory.max_total_viewer”
3. Set it’s value to “0“;(Zero)
1. Type “about:config” (no quotes) in the adress bar in the browser.
2. Find “browser.sessionhistory.max_total_viewer”
3. Set it’s value to “0“;(Zero)
Increase the Speed in Which Firefox loads pages
1. Type “about:config” into the address bar and hit Enter.
(Normally the browser will make one request to a web page at a time. When you enable pipeliningit will make several at once, which really speeds up page loading.)
(Normally the browser will make one request to a web page at a time. When you enable pipeliningit will make several at once, which really speeds up page loading.)
2. Alter the entries as follows:
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 10.
Set “network.http.pipelining” to “true”
Set “network.http.proxy.pipelining” to “true”
Set “network.http.pipelining.maxrequests” to some number like 10.
This means it will make 10 requests at once.
3. Lastly, right-click anywhere and select New-> Integer. Name it “nglayout.initialpaint.delay” and set its value to “0“;.(Zero)
This value is the amount of time the browser waits before it acts on information it receives. If you’re using a broadband connection you’ll load pages faster now.
Optionally (for even faster web browsing) here are some more options for your about:config (you might have to create some of these entries by Right Click –> New– > Interger or String
Optionally (for even faster web browsing) here are some more options for your about:config (you might have to create some of these entries by Right Click –> New– > Interger or String
network.dns.disableIPv6: set “false”
“content.notify.backoffcount”: set “5“; (Five)
“plugin.expose_full_path”: set “true”.
“ui.submenuDelay”: set “0; (zero)
“content.notify.backoffcount”: set “5“; (Five)
“plugin.expose_full_path”: set “true”.
“ui.submenuDelay”: set “0; (zero)
Reduce RAM usage to 10mb when Firefox is minimized:
This little hack will drop Firefox’s RAM usage down to 10 Mb when minimized:
1. Open Firefox and go to the Address Bar. Type in about:config and then press Enter.
2. Right Click in the page and select New -> Boolean.
3. In the box that pops up enter “config.trim_on_minimize”. Press Enter.
4. Now select True and then press Enter.
5. Restart Firefox.
2. Right Click in the page and select New -> Boolean.
3. In the box that pops up enter “config.trim_on_minimize”. Press Enter.
4. Now select True and then press Enter.
5. Restart Firefox.
These simple tweaks will make your web browsing with Mozilla Firefox 2-3 times faster and easier. And I think they are fairly easy to apply. Enjoy!
Now Keep Your Operating System Always With You - Make Pocket OS
Are you travel a lot and have a problem of working on new OS every time than this post is for you.
After reading this post completely you have your full featured Operating System
in your pocket with all important applications.Getting Started
To start doing this you need
- A pen-drive of atleast 4 GB.
- A computer with windows operating system on it.
- Universal USB maker software ( download it here ).
- Now you need any Linux Distribution But we prefer Linux mint ( Download It Hear ).
- Now your system is ready to rook.
- Just put your pen-drive in.
- Double click on Universal USB installers icon.
- Click on accept.
- Now select Your distribution(In our case Linux mint).
- Select image path.
- Select your drive.
- Set persistence (For 4 GB pen-drive it should be 2 GB and for 8GB pen-drive it can be 6GB).
- Check formate this drive button.
- Click on next.
Your drive is ready to rook
Just plug in this drive in any computer boot that with it and your own operating system is ready every whare
That's how you can make your own plug and play operating system
Play The Famous Snake Game On Your Youtube Player
 Youtube is the number one video sharing website in the world, with millions of videos and a large number of users.
Youtube is the number one video sharing website in the world, with millions of videos and a large number of users.You all must have played the famous "SNAKE GAME" in your childhood time. So wanna play it again.
Here, Recently I came across a most fascinating trick of a Youtube Player which really amazed me a lot and I loved it too.So here, I wanna share it with you all. Its a trick that would enable you to play the famous "Snake Game" within your video player.
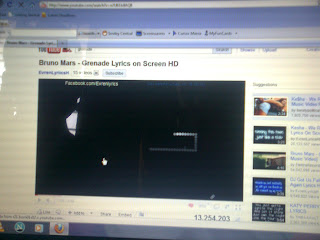
The trick is pretty simple, here is what needs to be done.
1. Start your Youtube Player.
2. Pause? the video at 00:00 time.
3. Press the Left arrow key on your keyboard.
4. Keep holding the Left key and press the Up arrow key.
5. The game would start, so release the keys and start playing Snake.
That's cool.........!! isn't it.....????
Now Customize Your Mouse Settings Firefox
To control mouse in Firefox and to scroll between tabs is a difficult task. So to over come this problem we have MouseControl is a Firefox extension that allows you to customize mouse settings to scroll between tabs, open/close tabs, duplicate current tab and change zoom levels from the mouse buttons.
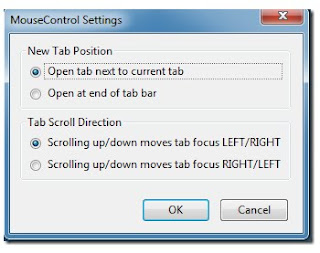
In MouseControl , to configure settings, click on the Options button (accessible from the Tools, Add-ons section)

In MouseControl , to configure settings, click on the Options button (accessible from the Tools, Add-ons section)
MouseControl also gives you facility to set scrolling options and choose between a right to left or left to right tab view. A list of numerous functions that you can perform with the mouse via this extension are as follows:
- To open a new tab: double click the right click button.
- To scroll between tabs: hold the right click button and use the middle scroll to move between tabs. Left click to return to original tab.
- To close a tab: click on the tab with the middle scroll.
- To open a closed tab: hold the middle scroll button for a second.
- Duplicate tab: hold duplicate tab after right clicking twice
- Zoom in/out: hold left mouse button and scroll up and down to zoom in/out. You can reset the zoom levels by clicking the middle scroll.
MouseControl is a use full part which helps in fast and effective use of mouse. MouseControl is quite a dynamic extension that adds new features to the mouse buttons in Firefox and makes it easier to manage tab functions via the mouse. This extension works with Firefox 3 and 4 (b8pre) .Install MouseControl
Tuesday, January 25, 2011
GTVHacker Jailbreaks Google TV, Runs Hulu

After a long wait of three months, a group of hackers named GTVHacker Dev Team has finally jailbroken Google TV to claim the $1000 bounty announced by developer Howard Harte. This jailbreak is based on several software and
hardware hacks. The hack includes opening up the Logitech Revue unit, and it even needs some tickling with the circuit board wires, making this hack a bit more complex than most people’s liking.
Here is the demo video of jailbroken Google TV:....
According to Howard Harte, this jailbreak opens up the entire Android app market for the device. To add to that, in near future you will be able to easily run streaming services like Hulu and many more, on your Google TV.
Nintendo Announces 3DS for Gamers [Hands-on Video]

In the recent past Nintendo 3DS made a lot of news because of being the first handheld console to display glassless 3D videos, and after waiting for so long
Nintendo has finally announced 3DS launch date for US & European customers. The handheld will be released on March 27
3DS will come in two colors viz., “Aqua Blue” & “Cosmos Black”. Nintendo will bundle a 2GB SD card (upgradable), charger, AC adapter, 3DS stylus, 6 augmented reality cards, and instruction manual with the handheld.
Starbucks Card Mobile app

Social network-driven phone systems: Skype and Google let you choose your own number. Google lets you choose which number will ring on which phones
as well as provide speech to text translations of voicemail. Enterprise IT will decide it is better to join in, rather than fight the tide.
Network Secutiry - 1
This is Abhishek with some new adventures of computer system.
In My last post series I saw you some download tricks.
Here In this series of post I have gone through various facts of the network and find out something insecurity in networking.
I here will present some loopholes in networks and also introduce you to the networking area.
You might just have to wait for one or two days for these posts.
Keep looking at our blog for updates.
In My last post series I saw you some download tricks.
Here In this series of post I have gone through various facts of the network and find out something insecurity in networking.
I here will present some loopholes in networks and also introduce you to the networking area.
You might just have to wait for one or two days for these posts.
Keep looking at our blog for updates.
If You Can't Delete Any File. It's For You
If you were trying to delete some files and you get any one of these below warnings from windows then the Hacking Tool of this week is most suited for you.
- Cannot delete file: Access is denied
- There has been a sharing violation.
- The source or destination file may be in use.
- The file is in use by another program or user.
- Make sure the disk is not full or write-protected and that the file is not currently in use.
Windows File Unlocker
This single-function system utility removes a file’s access restrictions. Unlocker is unobtrusive: it resides in the system tray; an Unlocker command appears in files’ right-click menus.
Description
The application removes file-access restrictions that prevent a user from moving, deleting, or renaming a file. The user right-clicks on a file and selects Unlocker, which displays information regarding the selected file, such as Path Locked, PID, Handle, and Process Path. This program also allows terminating a currently running process. In some cases, files cannot be accessed due to Windows file-access bugs, for which Windows informs the user the file is currently in use–even when it’s not.
Unlocker can effectively bypass this bug’s restrictions; it unlocks or disables whatever is preventing the user to access that file. This tool would be a lot easier to use if it allowed hot keys. Novices to advanced users will find this free application very useful.
Features
- Close any handle.
- Kill any process.
- Unload any Damn DLL. Note: You should be aware of the consequences before doing it.
- Delete index.dat . ‘index.dat‘ is System File which store your IE Web History
- Delete, Rename and Move any file you want without the permission of the owner
- Best of all. It is a Freeware!
How to Use it?
- Simply right click the folder or file and select Unlocker
- If the folder or file is locked, a window listing of lockers will appear
- Simply click Unlock All and you are done!
Download
You can download this free Utility at http://ccollomb.free.fr/unlocker/unlocker1.8.7.exe
How To Follow a Blog and email subscription of blog
I have seen a great problems in many users that they like this blog but do not know how to follow it.
I just here represents some screenshots taken by me to illustrate how to follow a blog? That might help you.

Some of My friends also asks me about how to receive email alerts of this blog's new post?
I have a solution of that too.
Just see the below screen shoots to subscribe the blog.
After the last post of the blog's first page you will surely see this .
Follow the Instruction(You have to use Google Reader(I think the best utility of google after its search engine))
I just here represents some screenshots taken by me to illustrate how to follow a blog? That might help you.

Some of My friends also asks me about how to receive email alerts of this blog's new post?
I have a solution of that too.
Just see the below screen shoots to subscribe the blog.
After the last post of the blog's first page you will surely see this .
Follow the Instruction(You have to use Google Reader(I think the best utility of google after its search engine))
Subscribe to:
Posts (Atom)




























