 10 reasons why PCs crash U must Kno
10 reasons why PCs crash U must KnoMonday, May 30, 2011
10 reasons why PCs crash U must Know
 10 reasons why PCs crash U must Kno
10 reasons why PCs crash U must KnoFriday, April 22, 2011
Free Sound Editing Software

Here are five free sound editing software that you can use without any restrictions:
- Audacity
Audacity is a very popular open source sound editing application. You can use it record live audio. You can use it to edit various audio formats and even cut, copy and mix them together. You can convert analog audio files into digital files. You can add various sound effects such as echo, phaser, reverse to the audio files. You can also enhance the audio quality through equalization, bass boost effect and normalize effects.|
Download Audacity
Platforms: Windows, Mac and Linux - Wavosaur
Wavosaur is free audio editor software that can be used to edit audio files. You can use it to batch convert audio files to desired formats. You do not have to install the application to use it. It does not add any information to the Windows registry. It can amplify the effects of the audio files. If supports VST plugins, multichannel wav files.
Download Wavosaur
Platforms: Windows (XP, Vista and Windows 7) - WavePad
WavePad Sound Editor is very user-friendly sound editor software that is available for free and has got plenty of features. It supports a wide range of audio formats. You can use it modify and manipulate all kinds of audio files. You can plenty of effects to the audio files such as normalize, amplify, equalizer, reverb, etc. The batch processing feature allows you to add sound effects to numerous audio files at one time.
Download Wavepad
Platforms: Windows and Mac - DJ Audio Editor
DJ Audio Editor is mp3 editing software with an intuitive interface. Even if you do not know much about sound editing, you can easily make use of it to manipulate audio files and add effects to it. It only supports mp3 files and has limited functions. It is a very light application and works very efficiently. It is a very good application if you are looking to make mp3 ringtones from the songs that present on your PC.
Download DJ Audio Editor
Platform: Windows (XP, Vista and Windows 7) - Power Sound Editor Free
Power sound editor free has got plenty of audio editing functionalities. You can edit large selection audio formats as well as add sound enhancing effects to it. You can also use it to remove disturbances through features like voice breath reduction. The free version lets you save the edited audio files in wav format. The deluxe version of this software brings to you plenty of unsurpassed audio editing features.
Download Power Sound Editor Free
Platform: Windows (XP, Vista and Windows 7)
Cool Computer Tricks
Looking cool computer tricks? Here is something that should pique your interest: Use Keyboard As Mouse, On Screen Keyboard and Transform your Windows XP in to Windows 7.

Use the Numerical pad for controlling the mouse pointer.
5 is for click.
+ is for double click
- for right click.
To use it go to start-> run and type osk


Just download it and install .
Download Seven Remix XP and transform your windows xp .

Use Keyboard As Mouse
When mouse isn’t working properly , this trick can be very helpful. To activate mouse keys all you do is press Alt+Left shift key + NumLock and click OK or press enter .
Use the Numerical pad for controlling the mouse pointer.
5 is for click.
+ is for double click
- for right click.
On Screen Keyboard
On screen keyboard is one of the coolest windows features that displays a virtual keyboard on the computer screen that allows people with mobility impairments to type data by using a pointing device or joystick..To use it go to start-> run and type osk


Transform your Windows XP in to Windows 7
If you are using Windows XP and want to experience Windows 7 without installing then here is Seven Remix XP transformation pack to transform Windows XP to Windows 7.With this simple app you can make your XP look like Windows 7 in just few clicks. It supports Windows XP, Windows 2003, Windows Media Center Edition and some other flavors of XP. Will work with only 32 bit edition of Windows.Just download it and install .
Download Seven Remix XP and transform your windows xp .

Saturday, April 9, 2011
How To Customize Your GRUB2 Boot Loader On Ubuntu

Got bored with default Ubuntu Grub bootloader? Looking for a nice GUI instead of Grub? Then try out Burg.This post is dedticated to all Ubuntu fans who love to customize there dafault Grub bootloader.
How to Install BURG?
1. Open a terminal window and type the following command,sudo add-apt-repository ppa:bean123ch/burg && sudo apt-get update
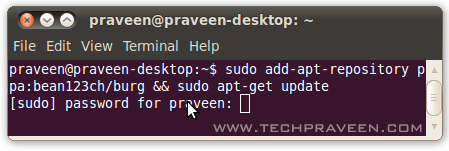
2. After its completion, close the terminal window.
3. Goto System –> Administration –> Synaptic Package Manager. In search box type “BURG” and hit enter.
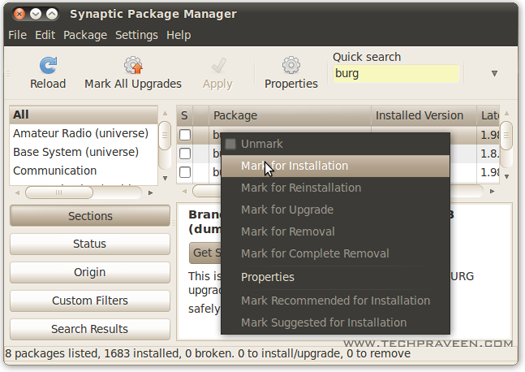
4. Right click on Burg mark it for installation then click apply.
5. The installation process will start.During installtion don’t make any change in first Burg settings window.Just click Forward.
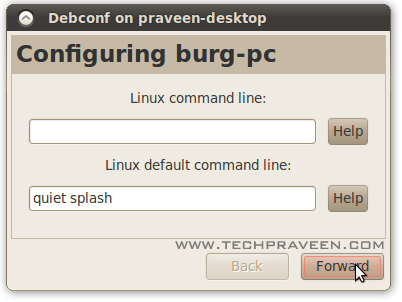
6. In the second window, choose your Ubuntu’s root drive, or if you have a separate /boot partition choose it instead.

7. Finally enter the following command in a terminal window and hit enter.
sudo update-burg
8. You can now restart and the Grub bootloader screen will be replaced by Burg. While at the boot screen, use these shortcuts press F1 for help, F2 for a list of themes, and F3 to change screen resolution.
Cool Isn’t it?
Make your Google search better!

Hand type the following prefixes and note their utility:
link:url Shows other pages with links to that url.
related:url same as "what's related" on serps.
site:domain restricts search results to the given domain.
allinurl: shows only pages with all terms in the url.
inurl: like allinurl, but only for the next query word.
allintitle: shows only results with terms in title.
A few things you might want to try with Google:
intitle: similar to allintitle, but only for the next word. "intitle:webmasterworld google" finds only pages with webmasterworld in the title, and google anywhere on the page.
cache:url will show the Google version of the passed url.
info:url will show a page containing links to related searches, backlinks, and pages containing the url. This is the same as typing the url into the search box.
spell: will spell check your query and search for it.
stocks: will lookup the search query in a stock index.
filetype: will restrict searches to that filetype. "-filetype:doc" to remove Microsoft word files.
daterange: is supported in Julian date format only. 2452384 is an example of a Julian date
cache:url will show the Google version of the passed url.
info:url will show a page containing links to related searches, backlinks, and pages containing the url. This is the same as typing the url into the search box.
spell: will spell check your query and search for it.
stocks: will lookup the search query in a stock index.
filetype: will restrict searches to that filetype. "-filetype:doc" to remove Microsoft word files.
daterange: is supported in Julian date format only. 2452384 is an example of a Julian date
phone: enter anything that looks like a phone number to have a name and address displayed. Same is true for something that looks like an address (include a name and zip code)
site:www.somesite.net " www.somesite. net"
(tells you how many pages of your site are indexed by google)
allintext: searches only within text of pages, but not in the links or page title
allinlinks: searches only within links, not text or title
Internet Error Codes and Meaning
Sometime you are browsing the internet and trying to open any website, your e-mail and any FTP sites , but you see different error codes there. You should be familiar with these error codes. You can solve these problems if you are well-known with the meaning of error codes.
Error Codes Meaning
400 This is bad request error, First check you may be typing wrong URL name and server could not understand your request.
401 You are trying to open any unauthorized access site or page. Check your username and password if you are trying to open any webpage.
403 You are trying to open any forbidden page and you are blocked by that domain.
404 Here you are trying to open the webpage that was removed or re-named, also check the URL spelling.
408 This is time out error. you should send the request with in time that the server set for you.
Saturday, April 2, 2011
6 Tips to Avoid Facebook Viruses and Spam Messages
Facebook, the biggest social network with 500 million users, provides an interface to hit an unsuspecting crowd with malware and viruses. These viruses aren’t very difficult to detect if you are cautious enough. These Facebook viruses appear on your wall in forms of a bizarre or eye-catching stories and videos and once the user has clicked/liked the link, it is already late. The next step will be getting rid of your Facebook virus which is a time-consuming process. Its better to avoid spam messages and trojan viruses in the first place.
How to avoid it?
1. Think before you Act. Viruses on Facebook are sneaky. The hackers and cybercriminals who want your information know that Facebook users will often click on an interesting post without a moment’s thought. If a post sounds a bit over-the-top like a headline out of a tabloid, this is your first warning sign.
2. Try to avoid Links and videos with Catchy words like “funniest ever,” “most hilarious video on Facebook,” or “you’ve got to see this.” Do some keyword research to see if the post in question comes up in a search engine with information about a current virus or trojan.
3. Check the poster of the Suspicious content. If you receive a message from someone you do not know, this is an obvious red flag. Facebook video viruses also tend to pop up in your news feed or on your wall from friends you haven’t talked to in a while. Unfortunately, it’s likely this friend has already fallen victim to the latest virus on Facebook. After clicking on the story themselves, the message was sent out to all of their friends as well.
4 Avoid messages that have been posted by multiple users as the virus spreads among your friends who were not so cautious. If a link with title such as “Sexiest video ever” shows up all over your feed from all kinds of people (perhaps friends you would not expect to make such a post), this is another warning sign. Similar direct messages are a likely variant of the notorious Facebook Koobface virus which has used this approach in the past.
5. Do not fall for the “typical” money-transfer schemes. Chat messages from friends needing funds will usually sound suspicious. Everything can’t be screened before posting, so money transfer scams and hoax applications still find their way on to Facebook. You should also avoid applications that claim to do a full “Error check” or fix security problems related to your profile.
6. Update your anti-virus software frequently. If you do accidentally click on a post before realizing it is a hoax, do not click on any further links or downloads. If it’s too late and you have already been infected, the Facebook virus removal process may be effortless if you have a good anti-virus program to catch the virus, trojan or other malware early on.
What’s Next?
These were few important tips to safeguard your facebook account but your job isn’t done yet. Once you have detected that the link/post on your facebook wall is Malicious you should Mark it as SPAM so that the facebook support will stop it from spreading further and infecting other users.
If you have ever fallen victim of any such Malicious Scheme, please share your experience with all the users in form of comments so that others don’t fall victim of it.
Thursday, March 31, 2011
Appeal from IIIT-Allahabad Students: Appeal from IIIT-A students about atrocities of ad...
Appeal from IIIT-Allahabad Students: Appeal from IIIT-A students about atrocities of ad...: "Appeal from IIIT-A students about atrocities of administration including Institute Director We the students of IIIT Allahabad are in ..."
Friday, March 11, 2011
Microsoft Windows Hidden Program
1- Private Character Editor
This program is for designing icons and Characters(Alphapet)
Click :start
Then :run
type :EUDCEDIT
.................................................. ..................................................
2- iExpress
This Program is for conerting your files to EXCUTABLE files
Click : start
Then : run
type : iexpress
.................................................. ..................................................
3-Disk Cleanup
This program used for cleaning harddisk to offer space
Click : start
Then : run
type : cleanmgr
.................................................. ..................................................
Program ............. CODE
__________ __________
Character Map = charmap
DirectX diagnosis = dxdiag
Remote Access phone book = rasphone
Registry Editor = regedit
File siganture verification tool = sigverif
Volume Contro = sndvol
System Configuration Editor = sysedit
Syskey = syskey
Click :start
Then :run
type :EUDCEDIT
.................................................. ..................................................
2- iExpress
This Program is for conerting your files to EXCUTABLE files
Click : start
Then : run
type : iexpress
.................................................. ..................................................
3-Disk Cleanup
This program used for cleaning harddisk to offer space
Click : start
Then : run
type : cleanmgr
.................................................. ..................................................
Program ............. CODE
__________ __________
Character Map = charmap
DirectX diagnosis = dxdiag
Remote Access phone book = rasphone
Registry Editor = regedit
File siganture verification tool = sigverif
Volume Contro = sndvol
System Configuration Editor = sysedit
Syskey = syskey
Thursday, March 10, 2011
Free download Bit Defender 12.0.12.1 with serial key

BitDefender Internet Security 12.0.12.1 keeps your Internet-connected family safe, without slowing down their PCs. It locks out viruses, hackers & spam, while providing parental control and firewall protection.
Features and Benefits
Confidently download, share and open files from friends, family, co-workers - and even total strangers- Protects against viruses and other malware using industry-leading technologyNEW
- Scans all Web, e-mail and instant messaging traffic in real-time
- Provides an unmatched detection rate of new threats based on two different proactive technologies
- Blocks spyware programs that track your online activities
- Blocks web pages that attempt to steal your credit card data
- Prevents personal information from leaking via e-mail, Web or instant messagingNEW
- Instant Messaging Encryption keeps your conversations private on Yahoo! and MSN Messenger
- File Vault securely stores personal information or sensitive files
- The two-way firewall automatically secures your Internet connection wherever you are
- Wi-Fi monitor helps prevent unauthorized access to your Wi-Fi network
- Parental Control blocks access to inappropriate websites and e-mail
- Limits kids’ access the Internet, games, etc. to specific times
- Makes it easy for you to manage the security of your network from a single location
- Reduces the system load and avoids requesting user interaction during game play
- Optimized scanning technology skips safe files for better scan speed and lower system load
- Antispam stops unwanted e-mail from reaching your Inbox
- Laptop Mode prolongs battery life
- Assistance with common issues built directly into the product
- Free technical support for the entire duration of the product license
http://thepiratebay.org/torrent/4444901/BitDefender_Antivirus_2009_Build_12.0.10_Final_with_Keygen
But for the same, u need to have a torrent client like utorrent, bit comet, etc.
As per my experience, i do sugget Bit torrent ..
Wednesday, March 9, 2011
Trick Viruses by Renaming Your Anti-Virus Program to Explorer.exe
There are a lot of viruses out there, but many of them follow the same pattern: they lock you out of your system and only let you visit their site, pretending to be anti-virus software. Here's a trick to squash them.
There's more than one way to kill a virus, but if something's locking you out of computer, the How-To Geek has a great way to trick it into letting your Anti-Malware tool run a scan:
Since most of the fake anti-virus malware needs you to be able to slightly use your PC, the one executable that it won't ever block is "explorer.exe", since they want you to be able to get online and go to their site and pay them-not so easy if you have no Start Menu.They recommend using the free, portable SUPERAntiSpyware to sneak in there and destroy that nasty virus
So just rename your favorite anti-malware application to explorer.exe, and you should be able to use it.
Tuesday, March 8, 2011
How to Get Facebook Email Address
Facebook has just new features in which it will give email addresses to users ,at this time facebook email id is not open to everyone ,you have to request invittation.In order to get a invite to this new service you need to visit following link where in you would be asked to click on the ‘Request Invite’ button.
http://www.facebook.com/about/messages/
 if you are lucky you will get the yourname@facebook.com email id as soon as possible .Please note that Your email address will match your public username, for example:
if you are lucky you will get the yourname@facebook.com email id as soon as possible .Please note that Your email address will match your public username, for example:
Profile: facebook.com/username
Then your email address will be
Email: username@facebook.com
If you don’t have a username you can go here facebook.com/username/ to get or click below
http://www.facebook.com/username/
http://www.facebook.com/about/messages/

Facebook-email-Invite
Profile: facebook.com/username
Then your email address will be
Email: username@facebook.com
If you don’t have a username you can go here facebook.com/username/ to get or click below
http://www.facebook.com/username/
Block Websites on your system!
Some times it becomes necessary to block a website on our Computers for one or other reason. You can easily and effectivily block access to a website by adding it to your Windows HOSTS file. Once the website is blocked in the HOSTS file, it will not appear in any of the browsers. That is, the website becomes completely unavailable.
1. Go to your HOSTS file which is located at:
C:\WINDOWS\SYSTEM32\DRIVERS\ETC for Vista and XP
C:\WINNT\SYSTEM32\DRIVERS\ETC for Win 2000
C:\WINDOWS for Windows 98 and ME
2. Open HOSTS with Notepad.
The default Windows HOSTS looks like this:
______________________
# Copyright © 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a “#” symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
#
127.0.0.1 localhost
_____________________________
3. Directly under the line that says 127.0.0.1 Localhost, you will want to type:
127.0.0.1 name of the URL you want to block
For example to block the website MySpace.com, simply type:
127.0.0.1 myspace.com
127.0.0.1 www.myspace.com
Other parts of MySpace could be blocked in a similar way:
127.0.0.1 search.myspace.com
127.0.0.1 profile.myspace.com
etc etc etc…
It is necessary to add a website with and without the “www.”. You can add any number of websites to this list.
4. Close Notepad and answer “Yes” when prompted.
5. After blocking the website, test it in any of the browser. If every thing is done as said above,the website must not appear in any of the web browsers. You should see a Cannot find server or DNS Error saying: “The page cannot be displayed”. I have also created a virus to block a website which automatically blocks a list of websites as specified in the source program.
Some people suggest that your add a website to the Internet Explorer ‘Privacy’ settings. This does not block a site. It only stops that site from using cookies.
1. Go to your HOSTS file which is located at:
C:\WINDOWS\SYSTEM32\DRIVERS\ETC for Vista and XP
C:\WINNT\SYSTEM32\DRIVERS\ETC for Win 2000
C:\WINDOWS for Windows 98 and ME
2. Open HOSTS with Notepad.
The default Windows HOSTS looks like this:
______________________
# Copyright © 1993-1999 Microsoft Corp.
#
# This is a sample HOSTS file used by Microsoft TCP/IP for Windows.
#
# This file contains the mappings of IP addresses to host names. Each
# entry should be kept on an individual line. The IP address should
# be placed in the first column followed by the corresponding host name.
# The IP address and the host name should be separated by at least one
# space.
#
# Additionally, comments (such as these) may be inserted on individual
# lines or following the machine name denoted by a “#” symbol.
#
# For example:
#
# 102.54.94.97 rhino.acme.com # source server
# 38.25.63.10 x.acme.com # x client host
#
127.0.0.1 localhost
_____________________________
3. Directly under the line that says 127.0.0.1 Localhost, you will want to type:
127.0.0.1 name of the URL you want to block
For example to block the website MySpace.com, simply type:
127.0.0.1 myspace.com
127.0.0.1 www.myspace.com
Other parts of MySpace could be blocked in a similar way:
127.0.0.1 search.myspace.com
127.0.0.1 profile.myspace.com
etc etc etc…
It is necessary to add a website with and without the “www.”. You can add any number of websites to this list.
4. Close Notepad and answer “Yes” when prompted.
5. After blocking the website, test it in any of the browser. If every thing is done as said above,the website must not appear in any of the web browsers. You should see a Cannot find server or DNS Error saying: “The page cannot be displayed”. I have also created a virus to block a website which automatically blocks a list of websites as specified in the source program.
Some people suggest that your add a website to the Internet Explorer ‘Privacy’ settings. This does not block a site. It only stops that site from using cookies.
Starting Page Makes Your Google Searches Completely Anyonymous
Google's a great search engine, but search privacy has long been a concern for some. If you want to search privately without leaving Google, Start Page is a simple webapp that can act as a proxy for your searches.
Starting Page operates just like any search: you enter terms, press search, and get results. In this case, however, you're still searching Google but Starting Page goes out and performs the search for you. This way Starting Page is tracked for performing the search and you're not, keeping your search private.
Wednesday, March 2, 2011
More than 50 Android apps found infected with rootkit malware
Google acts to remove apps after developer finds 'DroidDream' malware can take over phone and send personal details to remote server (updated)
More than 50 applications on Google's Android Market have been discovered to be infected with malware called "DroidDream" which can compromise personal data by taking over the user's device,
and have been "suspended" from the store.
Google removed the apps from the Market immediately on being alerted, but it is not clear whether it has removed them from devices to which they have been downloaded. As many as 200,000 Android devices could have been infected.
The revelation comes from Android Police, a news site on Google's operating system, which calls it "the mother of all Android malware", noting that its examination had found that it "steals nearly everything it can: product ID, model, partner (provider?), language, country, and userID. But that's all child's play; the true pièce de résistance is that it has the ability to download more code. In other words, there's no way to know what the app does after it's installed, and the possibilities are nearly endless."
Lookout, a security company, which in a blogpost lists the 50-plus apps discovered to be infected. (The list is also below, via Lookout.)
Smartphones running Google's Android software have become enormously popular and are reckoned to be close to taking over worldwide as the fastest-selling smartphone platform, ahead of Finland's Nokia. Its growth has been fuelled by the fact that the software is free to license, and for developers there is no charge or checks to putting apps on the Market – unlike Apple's iPhone App Store, which checks every app against a suite of tests for suitability before allowing it on its store.
That has led the Market to grow rapidly, but also makes situations like the latest one – which is not the first case of malware found on the Market – harder to avoid.
The malware was first discovered by a Reddit user, Lompolo, who spotted that the developer of one of the malware apps had also posted pirated versions of legit apps, using the developer name "Myournet". But two other developers' products have also been found to include DroidReam.
Lompolo noted that "Myournet" had "taken 21 popular free apps from the Market, injected root exploit [code] into them and republished". More worryingly, those had seen between 50,000 and 200,000 downloads altogether in just four days.
DroidDream contains code which can "root" – take complete control of – a user's decice, and send detailed information such as the phone's IMEI (International Mobile Equipment Identity) and IMSI (International Mobile Subscriber Identity) numbers and send them to remote servers. But as Android Police's team found, the code can go much further in rooting through a phone.
Update: details of how the root code works are here. Note that this is a "privilege escalation" attack - once the app starts it uses the fact that it has user privileges to jump out of its sandbox and root the phone.
It's a rather brutal reminder of the fact that Android's openness is both a strength and, at times like this, a weakness – though Google's rapid action, in which it pulled the apps from the Android Market within just five minutes of being alerted, is encouraging.
It now looks likely that security companies will begin to compete to offer antivirus and anti-malware products for Android devices – which, given its rapid growth, could prove a fertile area for them with PC sales flat.
If you have downloaded any of the apps below, you should contact your phone company.
Full list of infected applications published by "Myournet": • Falling Down • Super Guitar Solo • Super History Eraser • Photo Editor • Super Ringtone Maker • Super Sex Positions • Hot Sexy Videos • Chess • 下坠滚球_Falldown • Hilton Sex Sound • Screaming Sexy Japanese Girls • Falling Ball Dodge • Scientific Calculator • Dice Roller • 躲避弹球 • Advanced Currency Converter • App Uninstaller • 几何战机_PewPew • Funny Paint • Spider Man • 蜘蛛侠
Full list of infected applications published by "Kingmall2010″: • Bowling Time • Advanced Barcode Scanner • Supre Bluetooth Transfer • Task Killer Pro • Music Box • Sexy Girls: Japanese • Sexy Legs • Advanced File Manager • Magic Strobe Light • 致命绝色美腿 • 墨水坦克Panzer Panic • 裸奔先生Mr. Runner • 软件强力卸载 • Advanced App to SD • Super Stopwatch & Timer • Advanced Compass Leveler • Best password safe • 掷骰子 • 多彩绘画
Full list of infected apps under the developer name "we20090202″: • • Finger Race • Piano • Bubble Shoot • Advanced Sound Manager • Magic Hypnotic Spiral • Funny Face • Color Blindness Test • Tie a Tie • Quick Notes • Basketball Shot Now • Quick Delete Contacts • Omok Five in a Row • Super Sexy Ringtones • 大家来找茬 • 桌上曲棍球 • 投篮高手
More than 50 applications on Google's Android Market have been discovered to be infected with malware called "DroidDream" which can compromise personal data by taking over the user's device,
and have been "suspended" from the store.
Google removed the apps from the Market immediately on being alerted, but it is not clear whether it has removed them from devices to which they have been downloaded. As many as 200,000 Android devices could have been infected.
The revelation comes from Android Police, a news site on Google's operating system, which calls it "the mother of all Android malware", noting that its examination had found that it "steals nearly everything it can: product ID, model, partner (provider?), language, country, and userID. But that's all child's play; the true pièce de résistance is that it has the ability to download more code. In other words, there's no way to know what the app does after it's installed, and the possibilities are nearly endless."
Lookout, a security company, which in a blogpost lists the 50-plus apps discovered to be infected. (The list is also below, via Lookout.)
Smartphones running Google's Android software have become enormously popular and are reckoned to be close to taking over worldwide as the fastest-selling smartphone platform, ahead of Finland's Nokia. Its growth has been fuelled by the fact that the software is free to license, and for developers there is no charge or checks to putting apps on the Market – unlike Apple's iPhone App Store, which checks every app against a suite of tests for suitability before allowing it on its store.
That has led the Market to grow rapidly, but also makes situations like the latest one – which is not the first case of malware found on the Market – harder to avoid.
The malware was first discovered by a Reddit user, Lompolo, who spotted that the developer of one of the malware apps had also posted pirated versions of legit apps, using the developer name "Myournet". But two other developers' products have also been found to include DroidReam.
Lompolo noted that "Myournet" had "taken 21 popular free apps from the Market, injected root exploit [code] into them and republished". More worryingly, those had seen between 50,000 and 200,000 downloads altogether in just four days.
DroidDream contains code which can "root" – take complete control of – a user's decice, and send detailed information such as the phone's IMEI (International Mobile Equipment Identity) and IMSI (International Mobile Subscriber Identity) numbers and send them to remote servers. But as Android Police's team found, the code can go much further in rooting through a phone.
Update: details of how the root code works are here. Note that this is a "privilege escalation" attack - once the app starts it uses the fact that it has user privileges to jump out of its sandbox and root the phone.
It's a rather brutal reminder of the fact that Android's openness is both a strength and, at times like this, a weakness – though Google's rapid action, in which it pulled the apps from the Android Market within just five minutes of being alerted, is encouraging.
It now looks likely that security companies will begin to compete to offer antivirus and anti-malware products for Android devices – which, given its rapid growth, could prove a fertile area for them with PC sales flat.
If you have downloaded any of the apps below, you should contact your phone company.
Full list of infected applications published by "Myournet": • Falling Down • Super Guitar Solo • Super History Eraser • Photo Editor • Super Ringtone Maker • Super Sex Positions • Hot Sexy Videos • Chess • 下坠滚球_Falldown • Hilton Sex Sound • Screaming Sexy Japanese Girls • Falling Ball Dodge • Scientific Calculator • Dice Roller • 躲避弹球 • Advanced Currency Converter • App Uninstaller • 几何战机_PewPew • Funny Paint • Spider Man • 蜘蛛侠
Full list of infected applications published by "Kingmall2010″: • Bowling Time • Advanced Barcode Scanner • Supre Bluetooth Transfer • Task Killer Pro • Music Box • Sexy Girls: Japanese • Sexy Legs • Advanced File Manager • Magic Strobe Light • 致命绝色美腿 • 墨水坦克Panzer Panic • 裸奔先生Mr. Runner • 软件强力卸载 • Advanced App to SD • Super Stopwatch & Timer • Advanced Compass Leveler • Best password safe • 掷骰子 • 多彩绘画
Full list of infected apps under the developer name "we20090202″: • • Finger Race • Piano • Bubble Shoot • Advanced Sound Manager • Magic Hypnotic Spiral • Funny Face • Color Blindness Test • Tie a Tie • Quick Notes • Basketball Shot Now • Quick Delete Contacts • Omok Five in a Row • Super Sexy Ringtones • 大家来找茬 • 桌上曲棍球 • 投篮高手
Tuesday, March 1, 2011
5 Myths about Internet Safety
“Internet Safety” the term has been getting vague with the increasing virus outbreaks nowdays. PC Magazine once conducted a survey in which they asked the participants to rate their broadband ISP services and the results were astonishing. Most of users didn’t completely understand the seriousness of potential threats or how to protect their PCs. Here are the top 5 Myths about safe surfing over internet.
Myth 1 – I don’t keep important things on my PC, so I don’t have to worry about security. Your PC can be infected over internet
Long time ago,this was partially true… but the hybrid worms and viruses of today like Blaster, hidrag and others blindly spread across internet to thousands or millions of PCs in a matter of hours, without regard for who owns them, what is stored there, or the value of the information they hold for the sole purpose of wreaking havoc. Even if your computer is not attacked directly, it can be used as a zombie to launch a denial-of-service or other attack on a network or to send spam or pornography to other PCs without being traced. Therefore, your civic responsibility is to protect your PC so that others are protected.Myth 2 – I can protect my PC if I disconnect from the Internet or turn it off when I’m not using it.
Wrong. You are a target, If you connect to the Internet at all. You could download a virus when you connect to internet and it may not be activated immediately, not until you read your email offline days after. Viruses nowadays spread wildly through USB/Pen drives, pirated cd’s or torrents or file from networks. But now you can protect your business from internet threats with the top web security softwareMyth 3 – I can protect myself from viruses by not opening suspicious e-mail attachments. Some viruses simply get activated by reading or previewing an e-mail
Wrong again. The next virus you get may come from your best friend’s or boss’ computer if his e-mail address book was compromised for simulating an attack. Hybrid worms can enter through the Web browser through loopholes and it is possible to activate some viruses simply by reading or previewing an e-mail. You simply must have a PC-based antivirus package or a firewall.Myth 4 – I have a Macintosh (or a Linux-based system), not a Windows system, so I don’t have to worry about being attacked.
It is true that most attacks target Microsoft Windows–based PCs, but there have been attacks against Mac OS and Linux systems as well. Some experts have predicted that the Mac virus problem will get worse, because Mac OS X uses a version of Unix. And although these systems have some useful security features, they can still be attacked.Myth 5 – My system came with an Anti-virus package, so I’m protected.
Not quite. Firstly, if you haven’t activated your antivirus to scan incoming web traffic automatically, you don’t have a good Anti-virus and malware protection software. Secondly, new threats appear daily, so an antivirus package is only as good as its last update so its a must to activate the auto-update features to keep your guard up against the latest threats. Thirdly, an antivirus package can’t protect you from every threat. Malwares, spywares are running in the wild out there and every now and then malicious code penetrate weak systems. You need a combination of solutions, including, at minimum, antivirus, a personal firewall ,an anti spyware/malware package and a plan for keeping your operating system and software up to date with security patches.Sunday, February 27, 2011
How does Worms work ?
 People use e-mail more than any other application on the internet, but it can be a frustrating experience, with spam and especially e-mail worms filling our inboxes. Worms can spread rapidly over computer networks, the traffic they create bringing those networks to a crawl. And worms can cause other damage, such as allowing unauthorized access to a computer network, or deleting or copying files.
People use e-mail more than any other application on the internet, but it can be a frustrating experience, with spam and especially e-mail worms filling our inboxes. Worms can spread rapidly over computer networks, the traffic they create bringing those networks to a crawl. And worms can cause other damage, such as allowing unauthorized access to a computer network, or deleting or copying files.What’s a worm?
A worm is a computer virus designed to copy itself, usually in large numbers, by using e-mail or other form of software to spread itself over an internal network or through the internet.
How do they spread?
When you receive a worm over e-mail, it will be in the form of an attachment, represented in most e-mail programs as a paper clip. The attachment could claim to be anything from a Microsoft Word document to a picture of tennis star Anna Kournikova (such a worm spread quickly in February 2001).
If you click on the attachment to open it, you’ll activate the worm, but in some versions of Microsoft Outlook, you don’t even have to click on the attachment to activate it if you have the program preview pane activated. Microsoft has released security patches that correct this problem, but not everyone keeps their computer up to date with the latest patches.
After it’s activated, the worm will go searching for a new list of e-mail addresses to send itself to. It will go through files on your computer, such as your e-mail program’s address book and web pages you’ve recently looked at, to find them.
Once it has its list it will send e-mails to all the addresses it found, including a copy of the worm as an attachment, and the cycle starts again. Some worms will use your e-mail program to spread themselves through e-mail, but many worms include a mail server within their code, so your e-mail program doesn’t even have to be open for the worm to spread.
Other worms can use multiple methods of spreading. The MyDoom worm, which started spreading in January 2004, attempted to copy infected files into the folder used by Kazaa, a file-sharing program. The Nimda worm, from September 2001, was a hybrid that had four different ways of spreading.
What do they do?
Most of the damage that worms do is the result of the traffic they create when they’re spreading. They clog e-mail servers and can bring other internet applications to a crawl.
But worms will also do other damage to computer systems if they aren’t cleaned up right away. The damage they do, known as the payload, varies from one worm to the next.
The MyDoom worm was typical of recent worms. It opened a back door into the infected computer network that could allow unauthorized access to the system. It was also programmed to launch an attack against a specific website by sending thousands of requests to the site in an attempt to overwhelm it.
The target of the original version of MyDoom attack was the website of SCO Group Inc., a company that threatened to sue users of the Linux operating system, claiming that its authors used portions of SCO’s proprietary code. A second version of MyDoom targeted the website of software giant Microsoft.
The SirCam worm, which spread during the summer of 2001, disguised itself by copying its code into a Microsoft Word or Excel document and using it as the attachment. That meant that potentially private or sensitive documents were being sent over the internet.
How do I get rid of them?
The best way to avoid the effects of worms is to be careful when reading e-mail. If you use Microsoft Outlook, get the most recent security updates from the Microsoft website and turn off the preview pane, just to be safe.
Never open attachments you aren’t expecting to receive, even if they appear to be coming from a friend. Be especially cautious with attachments that end with .bat, .cmd, .exe, .pif, .scr, .vbs or .zip, or that have double endings. (The file attachment that spread the Anna Kournikova worm was AnnaKournikova.jpg.vbs.)
Also, install anti-virus software and keep it up to date with downloads from the software maker’s website. The updates are usually automatic.
Users also need to be wary of e-mails claiming to have cures for e-mail worms and viruses. Many of them are hoaxes that instruct you to delete important system files, and some carry worms and viruses themselves.
As well, some users should consider using a computer with an operating system other than Windows, the target of most e-mail worms. Most of the worms don’t affect computers that run Macintosh or Linux operating systems.
Awesome + Resourceful Web Portals
Check out the following Microsoft Web portals that caters to need of almost everyone. The Portal name is followed by a brief description.
1. Website Spark : It’s for small IT enterprises. Microsoft provides them the tools needed for Designing and development for FREE!.
There is no upfront cost for first 3 years. Terms and conditions do apply, but they seem to be obvious For eg : You need to deploy a website before 6 months, renew your subscription after few months, etc. Above all, it is for all budding webmasters!
2. Biz Spark : To me, bizspark.com is extension of websitespark.com. Fundamentally it is for Tech startup’s that need support and visibility. This one is meant for all techno-preneurs!
3. Dream Spark : FREE software’s ( like Visual Studio professional! ) for students. If you need a key you can write to me at paras@parasdoshi.in.
4. Microsoft Student to Business : To bridge the gap between Industry requirements and Student’s knowledge. The website has list of Job and Internship openings of various tech firms. it’s for all those who dream to be corporate czars!.
Wednesday, February 23, 2011
WordPress 3.0 – “Thelonius” Advantages
Todays second post I want to share with my users is advantages of new wordpress it is wordpress 3.0 . So lets check it. WordPress 3.0, the long-awaited major version update to the world’s most popular blogging platform. The software, codenamed “Thelonius” now running your millions of websites.
The last major version, WordPress 2.9 was downloaded more than ten million times, a measure of the software’s popularity.so with the latest version 3.0 wordpress is now ready as the best Content Management System (CMS) that is available to support personal, business, academic, and corporate Web sites as well as blogs.As this is a major release there are new features including a brand new Default WordPress Theme called TwentyTen, the ability to Customize Post Types and an excellent new Menu Manager.

First we just look at the features through this video
So let’s have a look at WordPress 3.0 features or advantages.
1) MU or Multi-User option :
Multi-User option is one of the best features of WordPress 3.0 that will allow you to manage multiple blogs with different permissions from a single admin panel. Alright, admit it we all have at least a couple of blogs to work with, right? So MU is a very good feature.
2) Post Types Customization :
Till WordPress 2.9, WordPress has always enabled you to publish two types of content within a blog. These we recognize as blog Posts and Pages. Now in WordPress 3.0 you are able to define your own extra content types and also give them their own attributes. So now users can create any kind of content they want3) New “Twenty Ten” the Ultimate New Theme of WordPress 3.0 :
WordPress 3.0 having a new default design theme called Twenty ten. you can see the live demo of this design on official WordPress website. As you understand according to the new name of default theme every year WordPress got a new default theme in wordpress 3.0.

4) New Custom Menu Management Feature :
Probably for users the most useful feature released with WordPress 3.0 is the brand new menu management system that has been included with the new version.New Custom Menu Management feature is also available in wordpress it allows in creation of custom menus combining posts, pages, categories, tags, and links for use in theme menus or widgets.Menu management should be the most popular new function of WordPress3.0. It allows you to completely control the site’s navigation menu. Through easy drag and drop interface, users can freely create various combination of links: internal links, external links, categories, etc. And you can embed these custom menu themes anywhere and treat them as widgets.

5) Multi-Site WordPress :
In addition a new Multi-Site feature has been incorporated due to the merging of WordPress with WPMU, so that you can now build several WordPress blogs with the same software installation. So now you can manage several different websites each with a different domain or subdomains all from within a single installation of WordPress. This facility is not enabled by default as it will not be required by most users.6) Custom Background and Image support system :
This option will help you create new theme for your blog in a matter of minutes.
7) Specific author templates :
Now it is possible in WordPress 3.0 to use the specific author templates. So, you can easily mark your own post or entry with your signature.
8) Canonical Plugins:
Canonical plugins available in WordPress 3.0. This means that from the moment it is launched you will be able to easily use your favorite plugins without being afraid that new release of WordPress will kill them
How To Use Gmail To Send Email From Joomla
Hi Friends, Some days ago I worked on Joomla Project in which I got one requirement that client want to use Gmail and Joomla together such that Joomla sends emails via Gmail. So I implemented it successfully, So I thought to share it here with my reader, So it can be helpful to any one.
Below are steps to use Gmail and Joomla together such that Joomla sends emails via Gmail :
1. Go to Global configuration > Server. Here you will have to change some setting in “mail settings”.
2. Set “Mailer” to SMTP Server.
3. “Mail From” will be username@gmail.com.
4. Set “From Name” to whatever you want. E.g. Your Company Name.
5. “Sendmail Path” – no changes.
6. Set “SMTP Authentication” Set it to yes.
7. “SMTP Username” – username@gmail.com.
8. “SMTP Password” will be your password of Gmail.
9. “SMTP Host” is gmail-smtp-in.l.google.com
Below is image of mail setting tab, So please set all things accordingly and then your Joomla will use Gmail to send email.

Below are steps to use Gmail and Joomla together such that Joomla sends emails via Gmail :
1. Go to Global configuration > Server. Here you will have to change some setting in “mail settings”.
2. Set “Mailer” to SMTP Server.
3. “Mail From” will be username@gmail.com.
4. Set “From Name” to whatever you want. E.g. Your Company Name.
5. “Sendmail Path” – no changes.
6. Set “SMTP Authentication” Set it to yes.
7. “SMTP Username” – username@gmail.com.
8. “SMTP Password” will be your password of Gmail.
9. “SMTP Host” is gmail-smtp-in.l.google.com
Below is image of mail setting tab, So please set all things accordingly and then your Joomla will use Gmail to send email.

How To Add Cool Emoticons In Facebook Chat Conversations
In this post I’ll show you how to add cool set of emotions in your facebook chat conversations . All what you need to do is to install free facebook emotions and restart your web browser.
1) Download facebook emotions from this link
2) Restart your web browser





9 Best Twitter Desktop Apps for Mac
Hello Friends,
The popularity of Twitter has increased tremendously in past few years. As a result a lot of Twitter Desktop applications are available to the users for download these days. These applications allow you to receive and post Tweets from your desktop without visiting your Twitter.com page.
To reduce your burden of finding the appropriate app for you from such a big pool of apps, we have compiled a list of Best Twitter Desktop apps available in the market. Earlier I had compiled a list of 20 Best Twitter Desktop Apps for Windows. Today I give you 9 Best Twitter Apps for Mac.
1. EventBox
This just-for-Mac app is a favorite of many because it supports Twitter, Facebook, Flickr integration, feed reading with Google Reader and internet trend watching with Reddit and Digg . Keyboard shortcuts, hotkeys, Instapaper integration, and photo uploads to Flickr and Facebook make EventBox pretty nifty. It’s also got a very slick interface with a navigation menu on the left-hand side.
2. Mac Lounge
This app is incredibly appealing for its dead simple, single column interface and respectable feature set. We, of course, love the multiple account support, but also appreciate saved searches, quick access to view followers and following, and tweet options to link to tweet, copy tweet, or copy tweet URL. There’s also an accompanying iPhone app, which syncs with the desktop version and greatly improves the app’s relevance.
3. Nambu
This really sophisticated Mac app should be more than enough for any and all of your Twitter needs. You’ve got access to your followers and friends, custom groups, search (integrated with FriendFeed and One Riot), trends, tr.im and pic.im integration, multiple accounts, Ping .fm integration, filters, and three view options for a one or many column view of tweets.
4. Sideline:
Sideline is just a search and trending topic app from Yahoo, but it does a darn good job at satisfying those specific needs. You can view current Twitter trends, select to see the three latest tweets or pop out as its own saved search, and create custom search groups as tabs.
5. Skimmer:It’s hard not to love this app. Not only is it beautiful to look at it, but it also tracks your favorite social sites. Skimmer’s certainly not an application for the social media beginner, but power users of Facebook, Flickr, YouTube, Blogger, and Twitter, will appreciate the aggregation of content, filtering options, view types, and enhanced content viewing experience.
6. Tweetie
A full-featured Twitter client which is available in free ad supported and ad-free versions. This Desktop app lets you view not only the tweets but also the entire conversation history leading to that tweet. It provides you with an independent compose windows that stay out of your way until you need them. Tweetie for Mac also has search trends to let you find out the hottest trend in Twitter. Other features include threaded DMs, user details, torn off search, bookmarklet, and preferences.
7. Twibble Desktop
Twibble is a bit of a riddle. It’s not a bad app when it comes to feature set, but it’s also not the most intuitive. You can manage multiple accounts, but all tweets are merged together in one stream. You can reply, DM, fav, RT, and copy tweets, but you’ll have to hover over the tweet to even know those behaviors are possible. You can also use keyboard shortcuts, filter your tweets for keywords, or conduct searches that open up in new windows, but Twibble just doesn’t seem to flow as easily as we’d like it to.
8. Twitterific
Lets you both read and publish posts or “tweets” using a clean and concise user interface designed to take up a minimum of real estate on your Mac’s desktop. The app shows a scrolling list of the latest tweets from your friends, or public feeds. Its features include multiple Twitter account support, auto refreshing, inline display of replies and DMs, shows no. of unread tweets, quickly delete tweets, auto show/hide new tweets, single click access to user pages and more.
9. TwitterPod:
This app isn’t known for its sophistication or advanced Twitter functionality. TwitterPod is a basic single column Twitter app with an inline browser and the ability to filter for just tweets with links. Its heyday has long since passed, but original fan boys and girls may still be using this for their twittering.
Subscribe to:
Posts (Atom)






























